This plugin offers integration with Amazon Container Registry (ECR) as a DockerRegistryToken source to convert Amazon Credentials into a Docker CLI Authentication Token.
Amazon ECR plugin implements a Docker Token producer to convert Amazon credentials to Jenkins’ API used by (mostly) all Docker-related plugins.
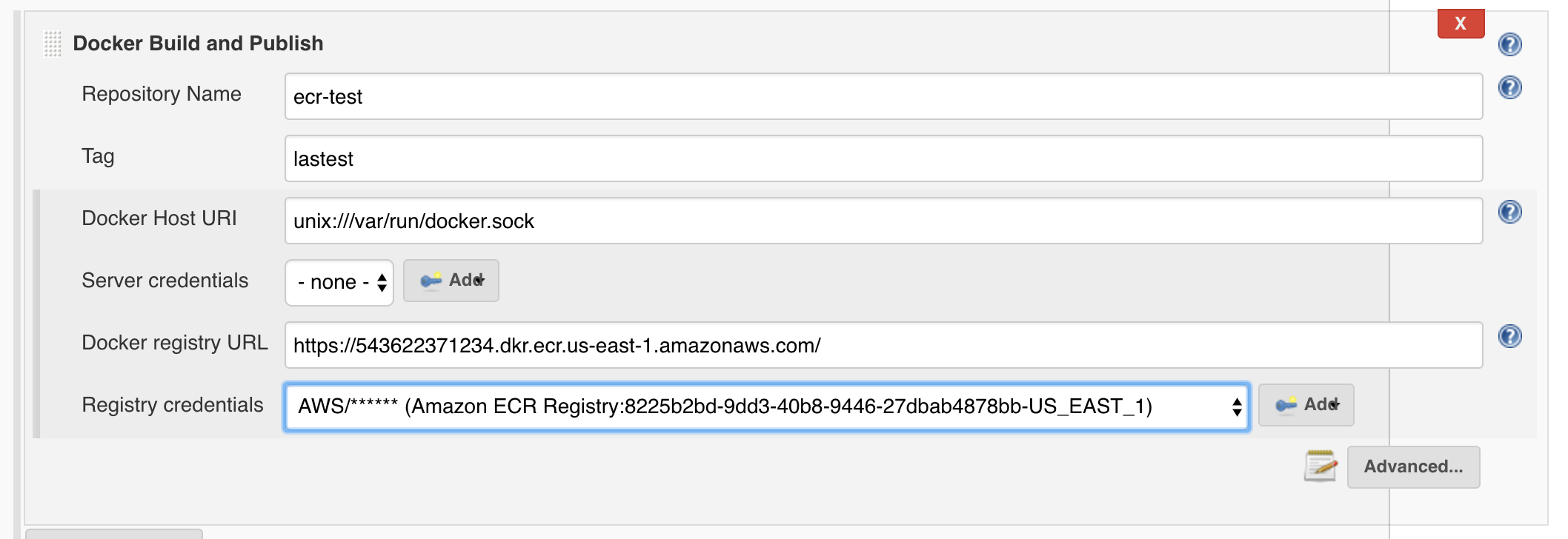
Thanks to this producer, you can select your existing registered Amazon credentials for various Docker operations in Jenkins, for example using the Docker Build and Publish plugin:
Navigate to the "Plugin Manager" screen, install the "Amazon ECR" plugin and restart Jenkins.
The plugin will use the proxy configured on Jenkins if it is set.
Recommended logger for troubleshooting, you have to take care where you publish these logs could contain sensitive information
- com.cloudbees.jenkins.plugins.amazonecr
- com.amazonaws
- org.apache.http.wire
- org.jenkinsci.plugins.docker.workflow
When using the Docker Pipeline Plugin, in order to obtain an ECR login credential, you must use the ecr provider prefix.
docker.withRegistry("https://your.ecr.domain.amazonws.com", "ecr:us-east-1:credential-id") {
docker.image("your-image-name").push()
}
If you experience authentication issues, you would try to remove user docker configuration files on the agents before to run the docker commands, something like this pipeline script.
node {
// cleanup current user docker credentials
sh 'rm -f ~/.dockercfg ~/.docker/config.json || true'
// configure registry
docker.withRegistry('https://ID.ecr.eu-west-1.amazonaws.com', 'ecr:eu-west-1:86c8f5ec-1ce1-4e94-80c2-18e23bbd724a') {
// build image
def customImage = docker.build("my-image:${env.BUILD_ID}")
// push image
customImage.push()
}
}
Unfortunately, testing against AWS isn't very straightforward, since you always need an AWS account with correct setup, which might incur some costs. Current tests try to make this as easy as possible. You need a user with read permission to ECR (AWS IAM policy AmazonEC2ContainerRegistryReadOnly should suffice) and an (empty) container registry. The test expect these details in the following environment variables:
export AWS_ACCESS_KEY_ID=<your-key-id-here>
export AWS_SECRET_ACCESS_KEY=<your-secret-access-key-here>
export AWS_REGISTRY_HOST=<some-number>.dkr.ecr.us-east-1.amazonaws.com
When those are set correctly, mvn test should run those tests successfully.
This plugin uses Google Java Code Style, which is enforced by the spotless plugin. If the build fails because you were using the "wrong" style, you can fix it by running:
$ mvn spotless:apply
to reformat code in the proper style.